The Nintendo DSi was surpassed by newer and better handhelds many years ago, but that doesn’t stop people like [Nathan Farlow] from attempting to break into the old abandoned house through a rather unexpected place: the (browser) window.
When the Nintendo DSi was released in 2008, one of its notable features was a built-in version of the Opera 9.50 web browser. [Nathan] reasoned an exploit in this browser would be an ideal entry point, as there’s no OS or kernel to get past — once you get execution, you control the system. To put this plan into action, he put together two great ideas. First he used the WebKit layout tests to get the browser into weird edge cases, and then tracked down an Windows build of Opera 9.50 that he could run on his system under WINE. This allowed him to identify the use-after-free bugs that he was looking for.
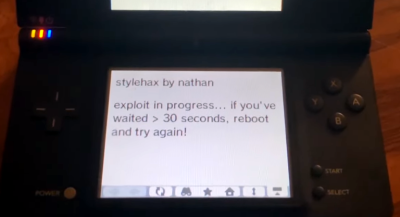 Now that he had an address to jump to, he just had to get his code into the right spot. For this he employed what’s known as a NOP sled; basically a long list of commands that do nothing, which if jumped into, will slide into his exploit code. In modern browsers a good way to allocate a chunk of memory and fill it would be a Float32Array, but since this is a 2008 browser, a smattering of RGBA canvases will do.
Now that he had an address to jump to, he just had to get his code into the right spot. For this he employed what’s known as a NOP sled; basically a long list of commands that do nothing, which if jumped into, will slide into his exploit code. In modern browsers a good way to allocate a chunk of memory and fill it would be a Float32Array, but since this is a 2008 browser, a smattering of RGBA canvases will do.
The actual payload is designed to execute a boot.nds file from the SD card, such as a homebrew launcher. If you want to give it a shot on your own DSi, all you need to do is point the system’s browser to stylehax.net.
If you’re looking for a more exotic way to crack into a DSi, perhaps this EM glitching attack might tickle your fancy?
Source: https://hackaday.com/2023/03/13/breaking-into-the-nintendo-dsi-through-the-browser-window/


